Accessibility Challenges with Digital Security Solutions

There were days of frustration last year when I couldn’t download apps via App Store on my iPhone. I sign out of my account and signed back in. I reset my iCloud account password. I refilled my Apple account with money too. But nothing worked. Then I realized my mistake. I had turned on Face ID for App Store and iTunes purchases. But why is that a mistake? After all, I have been using Face ID since 2018. I was using to unlock my phone and for other apps too. After researching online I found out I missed some finer points. It seems that I was supposed to double-click the side button on the confirmation screen but I was clicking the side button only once. Is it my mistake? Maybe, but what the screen told me via VoiceOver is “Confirm with Side button.” So, I did the same. Well, there is an animation that reads “Double click to confirm.” But many non-disabled users found that instruction unclear. This confirms that I am not alone. When I brooded over this problem, I thought how could a user with limited dexterity use this additional security method? What about other authentication methods? Are they accessible to everyone? The answer to these questions is this post.
What is digital security?
Protecting our digital identity, personal data, financial data, social data, and our presence from prying eyes, snooping software programs and other thieving methods is what is known as digital security. Digital security involves several services or processes like antivirus and internet security software, secure login methods, and other monitoring systems.
Why does digital security matter?
In the pandemic and post-pandemic world, our digital presence has increased into multifold, so do the security breaches, data record compromises, etc. In 2022 alone, the data breach damage costs reached up to 4.35 million $s approximately. Did you know? Almost 57% of the security breaches occur in the US alone. This makes digital security an utmost important factor and accessible security solutions are more needed so that end-users contribute to digital security.
In this post, we are not covering all the security solutions. Instead, we are discussing only the
authentication methods as they involve the end-users directly.
Traditional Authentication Methods
Traditional authentication methods are characterised by user input, text and number that users have to memorise or create or identify or resolve.
- Passwords
- PIN
- CAPTCHA
- Pattern locks
Passwords
Passwords are traditional, text-based, personalizable, and alphanumeric.
Accessibility challenges:
- Difficult to remember for users with learning/cognitive disabilities
- Becomes lengthier day by day
PIN
PIN is traditional, and numerically characterized.

Accessibility Challenges:
- Difficult to set up and use for users with learning disabilities – users who cannot deal with numbers in particular.
Pattern Lock
A traditional method that is used on mobile phones. Has three grid matrix and is highly personalizable.

Accessibility Challenges:
- Users without vision and with limited vision cannot use this as it is path based
- Users who have no or limited mobility would not be able to use this method.
CAPTCHA
CAPTCHA is an additional authentication method that confirms human access into the system.
Generally, they are image based where texts are embedded. Or users are asked to match or identify a particular pattern like blue cars or country flags etc.
Audio CAPTCHA is an alternative to visual CAPTCHA. They are voice-based. Users have to decode numbers or words from voices that are either blurred, fast, or robotic.
Accessibility Challenges:
Users with no vision and with limited vision find it difficult to perceive and solve CAPTCHA
Users with limited cognitive abilities find it difficult to solve CAPTCHA
Users who are Deaf-blind are left out in both visual and audio captcha.
Modern Authentication Method
Modern authentication methods are characterised by the usage of latest technologies like neural engines, biometric IDs, time sensitive inputs, multi-device dependencies.
- Fingerprint
- Facial Recognition
- Multifactor Authentication (MFA)
Biometric Authentication
Fingerprint and Facial Recognition are the prevalent methods used in biometric authentication.
Fingerprint
Users can create a biodigital ID using their fingerprints. They are stored either locally or online on servers.

Accessibility Challenges:
Users without mobility or limited mobility may not be able to use fingerprints as an
authentication method
Often, fingerprint authentication is disabled if the devices are idle and require additional
authentication like PIN/password to enable it which defeats the purpose.
Facial recognition
Users can create unique facial profiles and use them to authenticate themselves. They are stored on devices or on servers. They are used as a single sign-on method by other apps on mobile platforms.

Accessibility Challenges:
- Users with limited vision and without vision often find it difficult to set up Face IDs and use them though operating systems like iOS provide appropriate instructions and feedback through haptic and text which is spoken out by screen readers.
- People without mobility and with limited mobility may not be able to use this method
- More often than not, Face ID is disabled to prevent accidental authentication or inaccurate scans, and need additional methods like PIN to re-enable it.
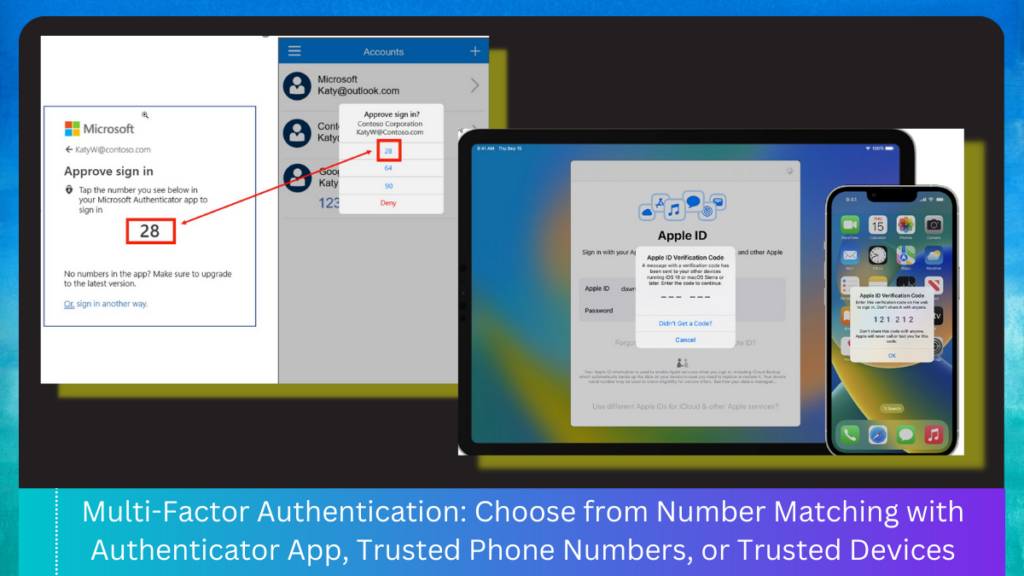
Multifactor Authentication (MFA)
Multifactor authentication is a process where more than one method of authentication is required to authenticate users while logging in to websites and apps. Currently, the industry uses random code generators from physical fobs, authenticator apps (mobile), SMS/email/call-based one-time passwords push-notification-based authentication etc.
Accessibility Challenges:
- Most or all of these methods place heavy cognitive overload on users.
- Users without vision and with limited vision cannot read the codes from physical fobs on their own; they need read help reading and entering the code which is time-sensitive.
- Users with limited vision and without vision need more time to memorize codes from authenticator apps like Microsoft Authenticator or Google Authenticator and enter into the system and they are time-sensitive. So, they may take more than one attempt and set of codes to complete the task and may fail resulting in account lock-outs.
- Users with cognitive disabilities face anxiety while switching between two devices or apps and the time-sensitive nature of MFA makes it more difficult for many users.
Changing trends
Owing to the increasing security breaches and data thefts, big tech companies want to do away with traditional authentication methods like passwords. The use of pass keys or passphrases that are system generated are gaining popularity. Apart from these methods, companies want their accounts to be used for single sign-on to third-party applications, hiding sensitive personal information and providing only necessary information for verification.
New authentication methods where user input is minimal are tried by Google and other tech companies. For example, while resetting account passwords, Google sends a push notification with a six-digit code to the secondary device. The same six-digit code is displayed on the primary device too. In this method, the users are asked to tap only to digit set on the secondary device where the notification is sent. This does not require users to memorize or copy or enter any code and thus decreases anxiety or other cognitive overload. One of the working groups of W3C, APA (accessibility platform architect) has also proposed some new accessible authentication methods like Decentralized Identifiers (DID) and Verifiable Credentials (VC) data model V1.0
that allows the users to authenticate themselves with locally provided DIDs and VCs without
compromising privacy. For example, a non-profit organization that supports people with disabilities can issue a digital identity which users with disabilities can use to authenticate themselves without providing a lot of personal data.
What needs to be done?
Securing the online/offline world is a collective responsibility of security experts and end-users too. But if the end-users need own up to the responsibility, then the security solutions must be accessible, usable, and inclusive. Tech products and services must provide more than one choice of authentication as ‘One size does not fit all’.
AI (Artificial Intelligence) based authentication methods that are robust, simple, inclusive, and require less efforts from users have to be developed. Researches must be conducted on how users respond to each security solution and the feedback must be incorporated by big tech companies and security companies.
Conclusion
Computers, mobile phones, websites – all these digital entities are invented only to assist human beings. Securing our digital presence and our data is possible if only those security solutions with which end-users interact are human-centric, inclusive, and usable by everyone. This needs active discussions between security experts, usability experts, accessibility experts and anyone who is interested in accessible digital security. Let’s join hands, spread the word and secure the digital future!
References
- Accessible and Inclusive Cyber Security: A Nuanced and Complex Challenge | Springer
- What is Digital Security: Overview, Types, and Applications Explained [Updated] (simplilearn.com)
- Some Critical Data Breach Statistics And Facts For People To Be Well Prepared To Fight Against Cybercrime
- CAPTCHA Accessibility
Article on how CAPTCHA systems are inaccessible to disabled users and some alternatives to consider when implementing CAPTCHAs on your website or mobile applications. - Accessibility and Cybersecurity Burnt in Captions
- Multifactor Authentication – Cognitive overload? | Lexdis 2.0
- Decentralized Identifiers (DIDs) v1.0 (w3.org)
- Verifiable Credentials Data Model v1.1 (w3.org)










